European Safer Internet Day
Arturai's study on how to protect your assets on-line
Set of agents deployed across the Internet that monitor attack traffiC.
Akamai maintains a distributed set of agents deployed across the Internet that monitor attack traffic.
Based on data collected by these agents, Akamai is able to identify the top countries from which attack traffic originates, as well as the top ports targeted by these attacks. (Ports are network-level protocol identifiers.) This section provides insight into port-level attack traffic, as observed and measured by Akamai, during the third quarter of 2012. It also provides observations on “Operation Ababil” attacks that targeted Akamai customers.
Attack Traffic, Top Originating Countries
During the third quarter of 2012, Akamai observed attack traffic originating from 180 unique countries/regions, down from 188 in the prior quarter. As shown in Figure 1, China overwhelmingly remained the source of the largest volume of observed attack traffic, accounting for nearly a third of the total, double the percentage observed in the second quarter. The United States remained in second place with a slight increase, originating 13% of observed attacks in the third quarter. The top 10 countries/regions remained unchanged quarter-over-quarter, with seven of them maintaining their positions on the list — Turkey, Russia and Taiwan were the only ones seeing movement. In terms of quarterly changes, only the United States and China saw increases, as noted above. China’s growth from the second quarter was fairly significant, and somewhat surprising.
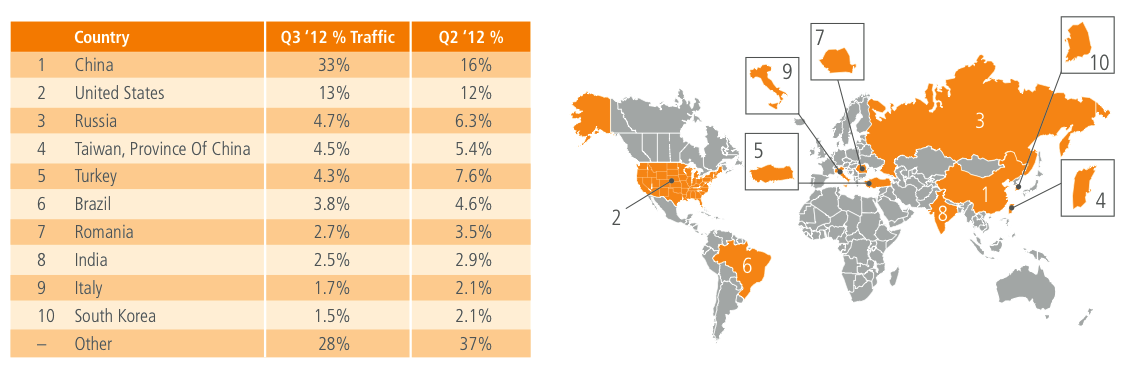
Figure 1: Attack Traffic, Top Originating Countries
Digging into the underlying data, it appears that for the top ports targeted by attacks observed to be originating in China, the number of attacks remains fairly high. However, for the other countries on the list, attack counts decline sharply after the top one or two targeted ports. In examining the regional distribution of observed attack traffic in the third quarter, we find that nearly 51% originated in the Asia Pacific/Oceania region, just under 25% in Europe, just over 23% in North and South America, and slightly more than 1% from Africa. In contrast to the decline seen in the second quarter, the Asia Pacific/Oceania region was the only one where any meaningful increase was seen in the third quarter, owing primarily to a doubling of the percentage of attack traffic observed to be originating from China.
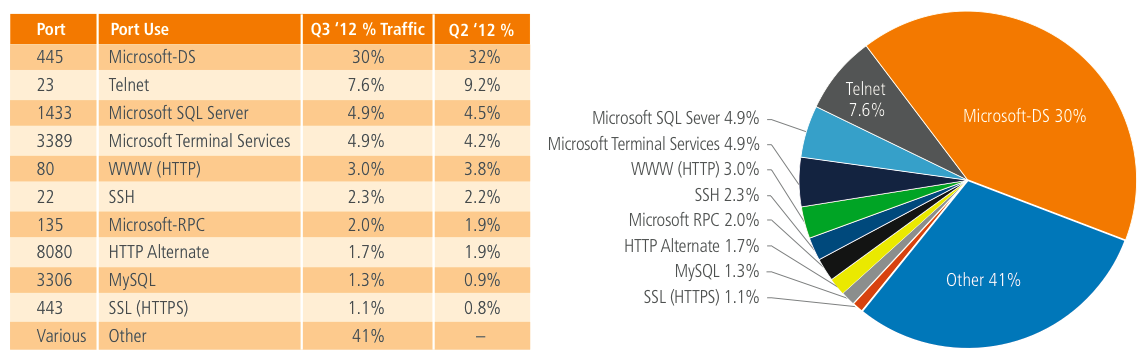
Figure 2: Attack Traffic, Top Ports Attack Traffic, Top Ports
DID YOU KNOW?
- For at least the last year, Port 23 (Telnet) has been the top targeted port for attacks observed to be originating in Turkey.
- China has been consistently responsible for the largest percentage of observed attacks since Q4 2011.
- Port 445 (Microsoft-DS) has been the top targeted port since the 2nd Quarter, 2008
Operation Ababil
On September 18, 2012, a group calling itself the “Mrt. Izz ad-Din al-Qassam Cyber Fighters” posted a proclamation to Pastebin.com 4 that it would be attacking a series of United States banks. These attacks were claimed to be in response to the controversial movie “Innocence of Muslim#, which also sparked violent protest across the middle east. The stated goal of the attackers was to continue impacting the operations of banks and other financial institutions until the movie was removed from the Internet. These attacks were labeled “Operation Ababil” by the attackers.
The pattern of the attacks was consistent throughout the series of offenses: a post was released each Monday on Pastebin.com stating which banks would be targeted, and the attacks started on Tuesday, continuing through Thursday evening. The first series of attacks (“Phase I”) occurred between September 18 and October 28, 2012, while a second round of attacks (“Phase II”) were called for, and started, the week of December 10, 2012.
Akamai was involved in protecting some of the banks and fiancial institutions that were targeted by Operation Ababil.
As a result, Akamai observed attacks with the following characteristics:
- Up to 65 gigabits per second (Gbps) of total attack traffic that varied in target and technique.
- A significant portion (nearly 23 Gbps) of the attack traffic was aimed at the Domain Name System (DNS) servers that are used for Akamai’s Enhanced DNS services.
- Attack traffic to Akamai’s DNS infrastructure included both UDP and TCP traffic which attempted to overload the servers and the network in front of them with spurious requests.
- The majority of the attack traffic requested legitimate Web pages from Akamai customer sites over HTTP & HTTPS in an attempt to overload the Web servers.
- Some attack traffic consisted of ‘junk’ packets that were automatically dropped by Akamai servers.
- Some attack traffic consisted of HTTP request floods to dynamic portions of sites such as branch/ATM locators and search pages. While the attackers claimed to be hacktivists protesting a movie, the attack traffic seen by Akamai is inconsistent with this claim.
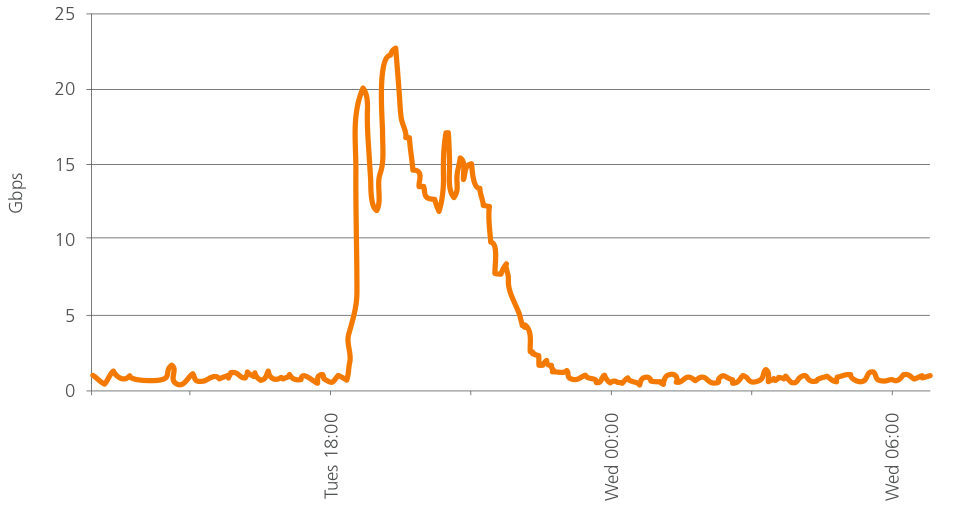
Figure 3: Incoming DNS Traffic (Gbps) Seen By Akamai’s EDNS Service During An Ababil Attack
The amount of attack traffic that was seen during these attacks was roughly 60 times larger than the greatest amount of traffic that Akamai had previously seen from other activist-related attacks. Additionally, this attack traffic was much more homogenous than we had experienced before, having a uniformity that was inconsistent with previous hacktivist attacks.
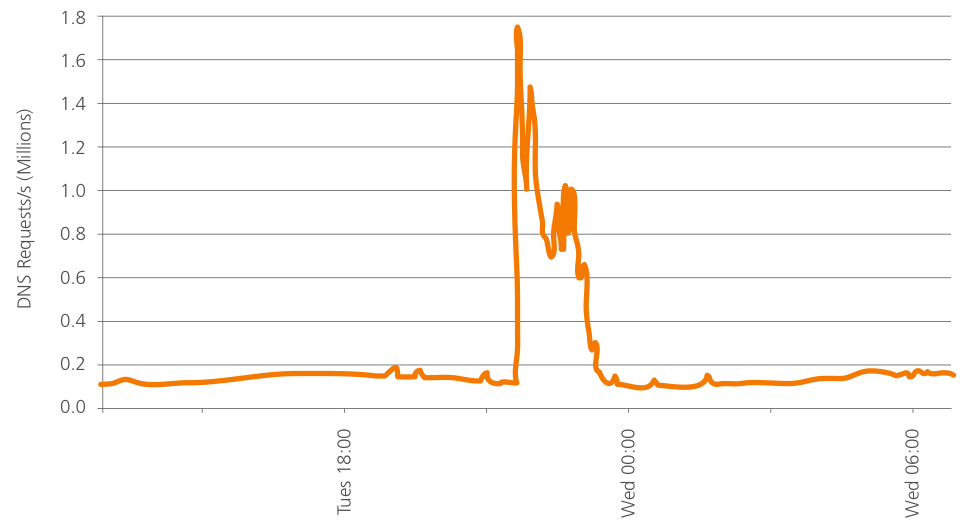
Figure 4: Incoming DNS Traffic (Requests Per Second) Seen By Akamai’s EDNS Service During An Ababil Attack
After investigation, it was discovered that the attacking nodes were members of a botnet consisting of compromised servers running “itsoknoproblembro” and other toolkits. This botnet is now referred to as “BroBot.” By being built from Web servers, BroBot exhibits the characteristics of high bandwidth per node and simplified command and control (C2), meaning that the attackers can bring a large volume of attack traffic to the intended target in a small amount of time. As shown in Figure 3 and Figure 4, the DNS traffic for one DDoS attack in Operation Ababil rapidly reached peak strength of nearly 23 Gbps and 1.7 million requests per second. The ability to rapidly grow the strength of the attack demonstrates very efficient BroBot command and control.
Akamai advises customers to take the following steps to protect their infrastructure from these types of attack:
- Protect their DNS: DNS is a critical service because when it fails, all other services fail (by essentially becoming unreachable). Akamai offers the Enhanced DNS (EDNS) service that uses the redundancy and availability of the Akamai platform to ensure uninterrupted resolution of customer hostnames.
- Protect against network-layer attacks: Network attacks attempt to flood the inbound connections into a target’s datacenter with overwhelming amounts of traffic. Akamai mitigates this by having a massive deployment footprint and load-balancing between servers, locations, and geographies.
- Protect the default page: A default page is the home page where the path ends in a “trailing slash” (for example, http://www.akamai.com/) that Web users see when they first come to your site. This is the page most commonly attacked in a DDoS and can be easily protected with basic caching. Protect redirect or splash pages: Splash pages are a special page such as a custom 404, maintenance, or typo page that gives Web users information, or redirects them to where the content is located. Often, these pages receive attack traffic destined for the default page, and can also be protected by basic caching.
- Protect dynamic sites: In those situations where caching is not a viable option, Akamai offers both rate controls to limit the amount of requests that an attacker can send and “waiting room” capabilities that can park traffic and keep legitimate users engaged while at the same time alleviating pressure on back-end applications. For some customers, we can also put these sites behind a user validation wall that requires users to log in to use the dynamic functionality.