EU General Data Protection Regulation (GDPR)
The EU General Data Protection Regulation (GDPR) is a new EU regulation that replaces the existing Data Protection Directive 95/46/EC, as well as many local laws implementing the Directive. The GDPR harmonizes data privacy laws across Europe to protect all EU citizens’ data privacy rights.
“GDPR is a game changer. State-of-the-art solutions are necessary. Akamai’s security services will help minimize the risks associated with your personal data processing activities."
Dr. Anna Schmits, EU Data Protection Officer, Akamai
GDPR: WHAT IS IT?
The EU General Data Protection Regulation (GDPR) is a new EU regulation that replaces the existing Data Protection Directive 95/46/EC, as well as many local laws implementing the Directive. The GDPR harmonizes data privacy laws across Europe to protect all EU citizens’ data privacy rights.
Under the new rules of the GDPR, the impact of non-compliance (e.g., failing to prove that the personal data processed has been adequately protected in case ofbreach) can have a material impact on the financial status of an organization, as well as severe consequences for its business leaders. Ultimately, the reputation of the organization is at stake.
The GDPR will be equally enforced by all European member states and will go into effect beginning 25 May 2018. Among its many requirements, the GDPR requires that companies, in order to minimize risks to the rights and freedoms of individuals, implement “appropriate technical and organizational measures to ensure a level of security appropriate to the risk.” These security measures must be in place before the May 2018 deadline. Given the significant volume of personal and sensitive data that is accessible via Internet-facing websites and web-facing applications, this is no small task.
In addition, the GDPR requires that organizations processing personal data be able to demonstrate that “appropriate” security measures are effectively and efficiently protecting the personal data processed. Meeting this obligation is complicated by the fact that organizations often utilize many third parties to provide specific data processing activities. While there may be a chain of data processing activities spread among a number of separate parties, the original organization — the so-called “Data Controller” — remains responsible for the protection of the personal data processed. Given the accountability established under the GDPR, it is an absolute must that Data Controllers have appropriate security measures in place and be able to provide evidence, especially in the unfortunate event of a data loss or breach, that these measures are effective.
What exactly is an “appropriate security measure” and what required evidence is expected to be delivered in a timely manner? According to the GDPR,appropriate security measures will be those that take into account the state of the art, the cost of implementation, and the scope, context, and purposes of processing, and balance these against the risks and impacts to the rights and freedoms of individuals. Of course, the perception of what is “appropriate” or “in balance” will be determined by the Data Protection Authority (DPA), who will no doubt look to industry best practice as a guide.
One tool for arriving at the required balance discussed above is the data protection impact assessment (DPIA), a process required in some cases under the GDPR to determine the potential impact of data processing activities. When conducting a DPIA, an organization must document in detail a number of factors, including:
- Envisaged data processing operations;
- The necessity and proportionality of these operations;
- An assessment of the risks of data breach associated with the operations;
- The measures envisaged to address these risks, including safeguards and security measures, and mechanisms to ensure protection of personal data.
The GDPR mandates a risk-based approach to data protection. Security obligations are not stated in a vacuum, but rather are to be developed based upon a thorough analysis and understanding of the risks that each processing activity may have for the individuals whose data is being processed. While this approach offers the necessary flexibility to allow organizations to apply reasonable measures in light of costs, system architecture, and related factors, it nevertheless requires a rigorous cost-benefit/risk review of everything that the organization does with personal data. In many cases, this is a significant task.
How successfully an organization can provide sufficient evidence of effective risk mitigation will depend upon its understanding of the relevant privacy risks as well as the strengths of the “state-of-the-art” security measures it chooses to implement in response to perceived risk.
Of course, an organization’s success also will depend upon the selection of partners that understand security and data protection obligations and take the necessary steps to protect their own systems. Akamai is committed to protecting the security of all the data transmitted over its platform, and has adopted an enterprise-wide information security program in accordance with the International Standard ISO/IEC ISO 2700x standard for information security management. Akamai is assessed annually against the ISO 27002 and the U.S. federal government’s FedRAMP standard. In addition, Akamai’s Secure CDN platform is assessed annually for compliance with the Payment Card Industry’s Data Security Standards and the Health Insurance Portability and Accountability Act. Akamai also undergoes annual Service Organization Control 2 Type 2 auditing and reporting.
HOW CAN AKAMAI HELP WITH GDPR COMPLIANCE?
Under the GDPR, evidence must be documented to show that that personal data processed by an organization is appropriately and sufficiently protected. In an interconnected world, where many web applications and websites contain or access personal data, this can be a big challenge. This challenge encompasses people, process, and technology. Akamai’s Intelligent Platform can be leveraged to help meet this challenge and offers a strong security strategy based on the best security professionals in the market, flexible and highquality processes, and recognized state-of-the-art technology.
n the following discussion, we provide four recommendations for approaching the security requirements under the GDPR and describe how Akamai Security Solutions can help organizations address major data processing risks.
Implement (2) “appropriate technical and procedural measures” that are risk-based and build upon industry best practice to protect web applications and websites.
Significant volumes of personal data are processed through Internet-facing applications. Companies and organizations are required under the GDPR to implement appropriate technical and organizational measures to secure the personal data under their control. Such measures should include security technologies designed to protect Internet-facing applications and websites from attacks intended to access personal data.
The Akamai Web Application Firewall (WAF) combines industry best practices such as those set out by the Open Web Application Security Project (OWASP) with intelligent scoring mechanisms to identify attack traffic. In addition, first-class security experts continuously monitor the web for new attacks.
The Akamai WAF is by design a risk-based threat protection service. It is built upon “risk groups” that can be used to immediately, effectively, and efficiently mitigate risks associated with the most sophisticated application layer attacks. By implementing the Akamai WAF, customers can demonstrate that they have taken reasonable steps to prepare themselves against many known and unknown threats.
An increasing amount of traffic traveling through the Akamai Intelligent Platform is API-based. The risk caused by APIs being “under-protected” is explicitly called out in the OWASP Top 10 of 2017 as an increasing risk that needs special attention. Akamai Kona Site Defender is focused on protecting API traffic. Kona Site Defender:
- protects RESTful APIs and traditional XML-based web services;
- mitigates DDoS attacks and data theft caused by excessive rate, slow post, parameter, and MITM attacks;
- is offered as a cloud solution and scales to the needs of the largest
- business asset owners and API publishers;
- provides analytics and value confirmation reports;
- provides SIEM integration.
Hard evidence that high-reputation best practices are effectively and efficiently implemented as part of an Information Security Management System forms an essential part of an organization’s risk mitigation, and will help to satisfy a Data Protection Authority by showing that appropriate security measures have been taken.
MAINTAIN WEB APPLICATION FIREWALL RULES
In the event of a security breach requiring the reporting of the loss of personal data to a DPA, it is extremely important that evidence is supplied to the DPA of the mitigation steps taken historically and the mitigation steps that will be taken in the future to ensure the impact is minimized.
For security measures to be effective, they must constantly be reviewed against new and changing threats. Akamai Security Optimization Assistance helps organizations to respond to the ever-changing threat landscape and provides evidence that they have actively anticipated and mitigated risks by creating and maintaining effective and efficient WAF rules.
Extensive reporting and evaluation is delivered containing the type, quantity, and probability of attacks in a given time period. As part of the Akamai Managed Kona Site Defender service, an Akamai security expert will proactively review security policies and make suggestions for ongoing adjustments of the WAF rules.
USE “STATE-OF-THE-ART” (3) TECHNOLOGY TO PREVENT DATA THEFT BY USING FULLY INTEGRATED DDOS AND APPLICATION LAYER PROTECTION WITH MEASURABLE EFFECTIVENESS.
Distributed Denial of Service (DDoS) attacks — combined with application layer attack vectors like SQL injection (SQLi), Local File Inclusion (LFI), Remote File Inclusion (RFI), and Cross-Site-Scripting (XSS) — are an extremely dangerous combination when it comes to the theft and leakage of personal data.
Often, separate and siloed solutions from different vendors that are unaware of each other’s existence are installed in your (cloud) datacenter. This approach is suboptimal and leads to delays and ineffective responses.
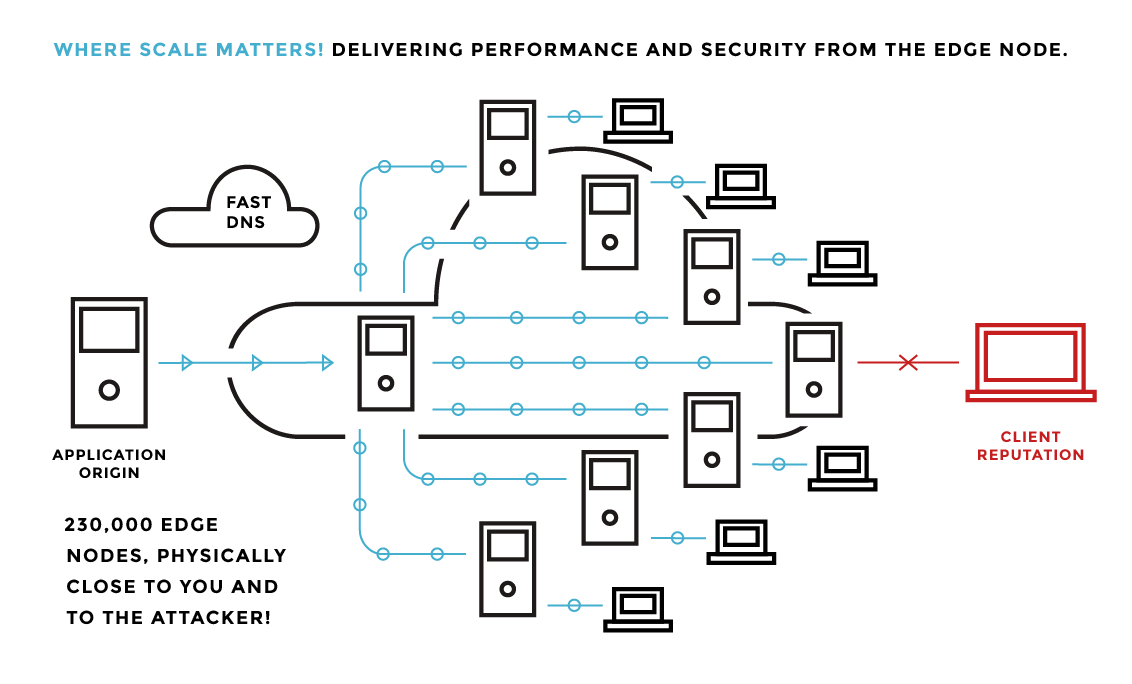
As the Akamai Web Application Firewall is part of the Akamai Intelligent Platform, it is designed to deliver customer content via the best available Edge Node for the user requesting certain web content (the WAF is part of Akamai’s core Content Delivery Network infrastructure). The best available Akamai Edge Node is, in many cases, the Edge Node that is physically closest to the user requesting your web content. The Akamai Intelligent Platform consists of a worldwide finegrained network of more than 230,000 Edge Nodes that run in more than 1,600 networks in more than 130 countries. The result is that attackers are stopped as soon as they try to reach corporate websites or web applications via the Akamai Edge Node — not just before the attack hits your corporate website or application server in your datacenter, where it becomes cumbersome to absorb all the load and to detect and mitigate the attack. Expensive oversized equipment needs to be bought and managed, or hybrid solutions need to be implemented with uncertain costs associated. The Akamai WAF is installed on thousands of Edge Nodes and absorbs the entire load smoothly while mitigating the attack at no extra capital cost to the organization. Application layer DDoS attacks, and attacks using ports other than ports 80 or 443, are immediately stopped at the Akamai Edge Node.
Specific customers’ WAF rules are quickly rolled out across thousands of relevant Edge Nodes protecting all the organizations’ web-facing resources all over the globe. This unique and innovative approach means that Akamai is better positioned than any other security vendor to protect the whole data processing and data distribution chain of personal data of any organization with any kind of Internet presence.
The effectiveness of the Akamai WAF can be increased further by adding the reputation of the IP addresses accessing your web resources. Akamai’s Client Reputation database sees 1 billion IP addresses each quarter. A small percentage of these are deemed to be malicious and rated on a scale of 1 to 10, and can be blocked by the customer using WAF rules. Every day, hundreds of millions of IP addresses are analyzed for malicious activity. This innovative approach results in a measurable effectiveness, 4 in most cases, with an accuracy of more than 95%. Evaluation of the effectiveness of the implemented security control is an important part of the GDPR compliance process.
Credential (username/password) theft can very easily lead to the loss of sensitive personal data. Following a recent large leakage of passwords on the Internet, researchers found that 8.8% of these credentials use one of seven very simple passwords (e.g., 123456, password, etc.). People tend to choose simple passwords that they can easily remember, and people reuse passwords often. Once credentials are hacked, it’s possible that multiple data sources areexposed. Attackers use sophisticated botnets to automatically and rapidly access websites worldwide using stolen credentials.
Akamai is well positioned to mitigate these risks. Akamai Bot Manager Premier installed on Akamai Edge Nodes can inspect and reject traffic to your web resources based on credential abuse-specific reputation.
CONTROL ACCESS OF THIRD PARTIES (E.G., CONTRACTORS) TO PERSONAL DATA
Organizations often must provide access to their network assets to third-party vendors necessary to operations. Such access, however, puts personal data and security generally at greater risk.
Akamai can help customers mitigate this risk by providing greater control and security for such connections. Akamai Enterprise Application Access (EAA) is focused on managing access to applications irrespective of where they reside, in a local datacenter or in the cloud. Akamai EAA ensures maximum control over who has access to which resources without the necessity to set up a complicated and costly Virtual Private Network (VPN) infrastructure.
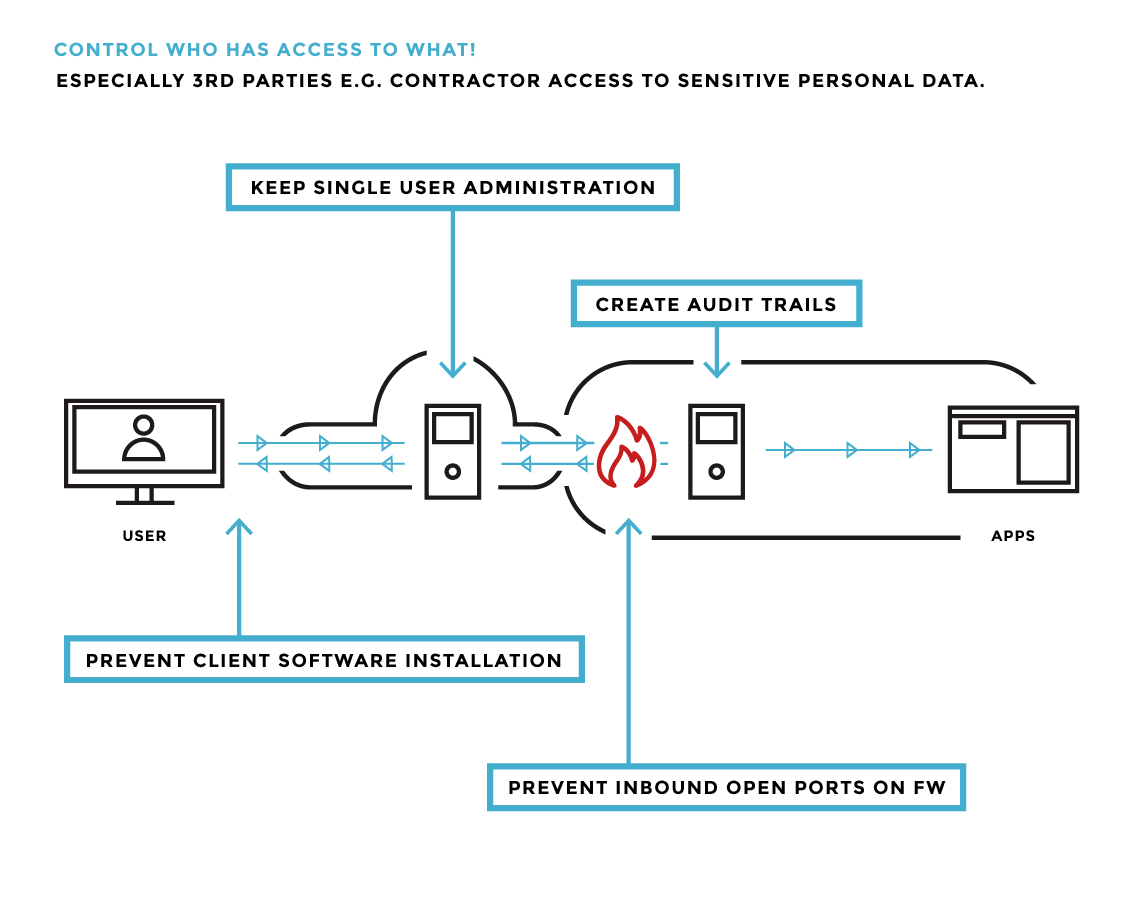
Akamai EAA can also be used alongside existing infrastructures. It is designed in such a way that firewalls can do what they should do: block unwanted inbound traffic. Akamai EAA makes it possible to close all Inbound ports. All incoming traffic will be managed and all unauthorized access will be blocked. Risk of unauthorized access is mitigated. Audit trails of contractor and user activity can be secured in an appropriate way, which simplifies documentation for any required data protection impact assessment or audit.
CONCLUSION
The GDPR requires a risk-based approach to data protection and asks for hard evidence that risks are continuously mitigated sufficiently. All organizations that process in any way the personal data of individuals in the EU must be prepared to demonstrate that they have taken strong steps to protect the personal data under their control. Akamai has developed and operates the world’s largest and most advanced cloud-based Intelligent Platform for securely distributing and accelerating web content. Leveraging the security knowledge and expertise of Akamai helps customers to protect their data assets, including personal data protected under the GDPR, against loss and unlawful access. Akamai can help with concrete steps to further customers’ efforts at GDPR compliance.
By implementing the Akamai Web Application Firewall (WAF), customers can demonstrate that they have taken steps to prepare themselves against many known and unknown threats. The WAF combines industry best practices with intelligent risk-based scoring mechanisms to identify attack traffic. Highly trained Akamai security experts help organizations to respond to the everchanging threat landscape and provide evidence that organizations have actively anticipated risks by creating and maintaining effective and efficient WAF rules.
In addition, the implementation of a harmonized and integrated DDoS and application layer solution mitigates the risk of multi-vector attacks focused on stealing personal data. Last but not least, Akamai helps customers in limiting employee and/or contractor access to only the applications and data required, maintaining audit trails of who accessed which resources when, providing mechanisms to meet and demonstrate required personal data access controls. Akamai is determined to help business owners manage the risks incurred by the new privacy regulation.
Author: Erik van Veen, CISSP, Akamai Technologies
Sources
1) See GDPR Article 33(7)
2) See GDPR Article 24(1)
3) See GDPR Article 24(1) and Article 25(1 and 2)
4) See GDPR Article 74